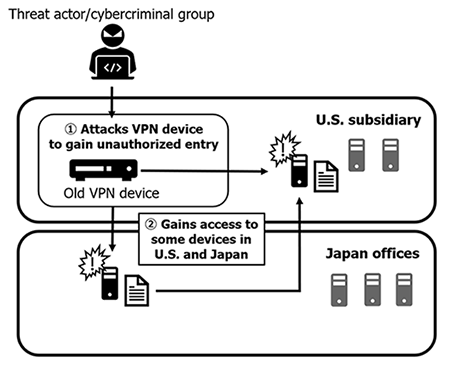
In an update post summarising the results of its (now-completed) investigation carried out with the help of specialist companies, Capcom said its internal systems are now “near to completely restored”. The attack had encrypted data on Capcom devices, and installed a message demanding Capcom contact the hacking group responsible. As for how the attack happened, Capcom explained that unauthorised access to the company’s internal network was acquired in October 2020 through an old backup VPN at Capcom USA. It seems Covid-19 had a hand in creating conditions for the attack to be successful, as although Capcom had already started switching to newer VPN devices, the growing strain on the company’s network due to working from home meant the older VPN was kept as “an emergency backup in case of communication issues”. This VPN became the target of the cyber attack, and through this the attackers were able to compromise devices at Capcom’s US and Japanese offices, leading to the theft of information. Although some perimeter measures were already in place, Capcom had been in the process of adopting additional defensive measures (a SOC server and EDR), but “had been forced to prioritise infrastructure improvements necessitated by the spread of Covid-19”. This meant the security measures had not yet been implemented by the time of the attack. The external specialist companies concluded the incident was a “malicious, multi-faceted attack that would be difficult to defend against”, Capcom said. Having established a new Technology Security Oversight Committee, Capcom plans to continue strengthening its security. Along with implementing that SOC service and EDR, it’s already cleaned all compromised devices and improved management methods for VPNs. It’s also made efforts to raise employee awareness of security, and strengthened internal systems with regular verification methods. The cumulative total for information verified to be compromised now stands at 15,649 people, down 766 from the previously-thought total. Capcom reaffirmed that credit card details and customer details have not been impacted. We don’t yet know what sort of damage that compromised personal and corporate data has caused, however, as Capcom is currently unable to confirm this. Capcom also reiterated that it did not make contact with the threat actor, under advice from law enforcement, and “is not aware of any ransom demand amounts”. “Capcom would once again like to reiterate its deepest apologies for any complications or concerns caused by the incident,” the post concluded. The update is largely focused on personal data, and there’s little mention of the large amount of internal corporate information that was splashed across the internet following the attack. Stolen information from the ransomware attack included previously-unannounced ports, release dates and in-progress projects. There’s a Resident Evil showcase scheduled for later this week, so some of these may get a proper announcement on Thursday. In the meantime, don’t trust any early access invitations for Resident Evil Village, as Capcom has warned these are part of a phishing scam.